.jpg)
Preparing Legacy Systems for Common Criteria Certification
10
min reading time
Understanding Common Criteria Certification Fundamentals
The Common Criteria certification process represents a globally recognized standard for evaluating IT product security. This framework establishes consistent, high-standard security evaluations across different jurisdictions, enabling international acceptance of security certifications. For organizations with legacy systems, understanding these fundamentals becomes critical for successful preparation.
The certification framework operates through systematic evaluation against predefined security requirements. A dedicated management committee oversees standard implementation, ensuring consistency across evaluations. The core objectives include standardizing security evaluations globally, eliminating redundant evaluations, enhancing certification cost-effectiveness, and improving availability of evaluated products.
Becoming Common Criteria certified requires systematic preparation and strategic planning for legacy systems. The evaluation process examines security functions, assurance measures, and documentation quality. Organizations must demonstrate that their systems meet specific security requirements at the chosen evaluation assurance level.
Legacy System Challenges in Common Criteria Compliance
Technical Integration Complexities
Legacy systems present formidable obstacles when pursuing Common Criteria compliance. Deep infrastructure integration creates complex dependencies that resist straightforward modification. These systems often feature difficult upgrade paths, making security enhancements challenging to implement without disrupting critical operations.
System architecture constraints limit the implementation of modern security controls. Legacy platforms may lack native support for current encryption standards, access control mechanisms, or logging capabilities required for certification. The interconnected nature of these systems means that changes in one component can trigger unexpected consequences throughout the infrastructure.
Operational and Support Limitations
Operational challenges compound technical difficulties. Many legacy systems operate without vendor support, leaving organizations to manage security updates independently. Missing security patches create vulnerabilities that must be addressed through compensating controls, adding complexity to the certification process.
Monitoring constraints present additional hurdles. Legacy systems often provide limited logging capabilities, insufficient visibility into system operations, and inadequate incident response mechanisms. These limitations make it difficult to demonstrate the continuous monitoring and security assurance required for Common Criteria certification.
Strategic Implementation Approaches for EAL Compliance
Assessment and Planning Framework
Successful preparation begins with thorough system evaluation. Organizations must conduct architecture reviews, dependency mapping, and security gap analyses. This assessment identifies specific areas requiring attention and helps prioritize remediation efforts.
Selecting the appropriate evaluation assurance level depends on your system’s security requirements and risk profile. EAL selection directly impacts the depth and rigor of your security evaluation. Higher EAL levels demand more extensive documentation and testing, while lower levels may be sufficient for systems with limited security requirements.
The Common Criteria certification process demands thorough documentation and evidence preparation. Organizations must document security policies, procedures, and technical implementations. This documentation serves as evidence during the evaluation process and demonstrates compliance with certification requirements.
Modernization Strategies
Strategic modernization options include rehosting, refactoring, rearchitecting, and complete replacement. Each approach offers different benefits and challenges for achieving Common Criteria legacy systems compliance.
- Rehosting moves applications to modern infrastructure while maintaining existing code. This approach provides immediate security improvements through updated operating systems and hardware platforms. However, it may not address fundamental architectural security limitations.
- Refactoring involves modifying existing code to improve security and maintainability. This approach allows organizations to address specific security vulnerabilities while preserving core functionality. The process requires careful planning to avoid introducing new vulnerabilities.
- Rearchitecting redesigns system components to meet modern security standards. This comprehensive approach addresses fundamental security limitations but requires significant investment and planning. Organizations must balance security improvements against operational disruption.

Common Criteria Readiness – Building an Internal Certification-Ready Operating Model
Preparing legacy systems for Common Criteria certification requires more than technical adjustments, it also requires an internal operating model that supports clear scoping, structured collaboration, and consistent alignment with CC requirements. Establishing a “CC-readiness” foundation enables organizations to manage complexity effectively, especially when legacy components and modernized elements must coexist.
Establish Clear Ownership and Governance
Effective Common Criteria preparation begins with assigning well-defined responsibilities. Organizations should designate a CC program owner who oversees:
- coordination of evidence and supporting materials
- communication between development, security, and compliance teams
- mapping organizational processes to CC expectations
- aligning security functions with TOE boundaries and evaluation scope
This governance model provides clarity across teams and ensures that every stakeholder understands how their work contributes to the certification effort.
Adopt a Documentation-Aligned Workflow
Documentation quality is central to Common Criteria, but readiness is not about producing more documents, it is about embedding traceability and clarity into day-to-day work. A documentation-aligned workflow helps organizations:
- maintain accurate descriptions of security functional requirements (SFRs)
- ensure design choices support the required security assurance requirements(SARs), which evaluators use to verify the strength and correctness of the implementation
- preserve institutional knowledge that may otherwise be fragmented in legacy environments
This cultural shift ensures that evidence development becomes a natural part of the process, not a last-minute task.
Enable Cross-Functional Security Alignment
Legacy modernization and certification succeed when development, operations, and security teams operate from a shared understanding of CC constraints. A CC-ready operating model should ensure that:
- modernization decisions respect TOE scope and defined security claims
- architectural changes are evaluated for impact on SFR/SAR fulfillment
- teams understand how each modification affects evaluators’ expectations
This alignment reduces inadvertent inconsistencies and helps maintain a coherent security narrative throughout the product.
Conduct Internal Readiness Checks
Before engaging in formal evaluation, organizations benefit from internal readiness checks that provide early visibility into structural or architectural gaps. These assessments help teams:
- validate that technical implementations support stated SFRs
- confirm that security behaviour is consistent across legacy and modernized components
- identify areas requiring clarification or refinement before external evaluation begins
These recurring checks ensure the project remains aligned with certification requirements as work progresses.
Leverage Professional Support as a Strategic Advantage
Expert guidance strengthens the internal operating model and helps organizations navigate CC-specific expectations confidently. Engaging with an accredited laboratory early provides clarity on:
- interpretation of SFR/SAR requirements
- appropriate scoping of the TOE
- documentation expectations for legacy environments
- potential risks related to modernization paths
CCLab’s consulting support helps organizations streamline preparation, optimize documentation, and avoid costly rework, resulting in a more predictable, efficient certification journey.

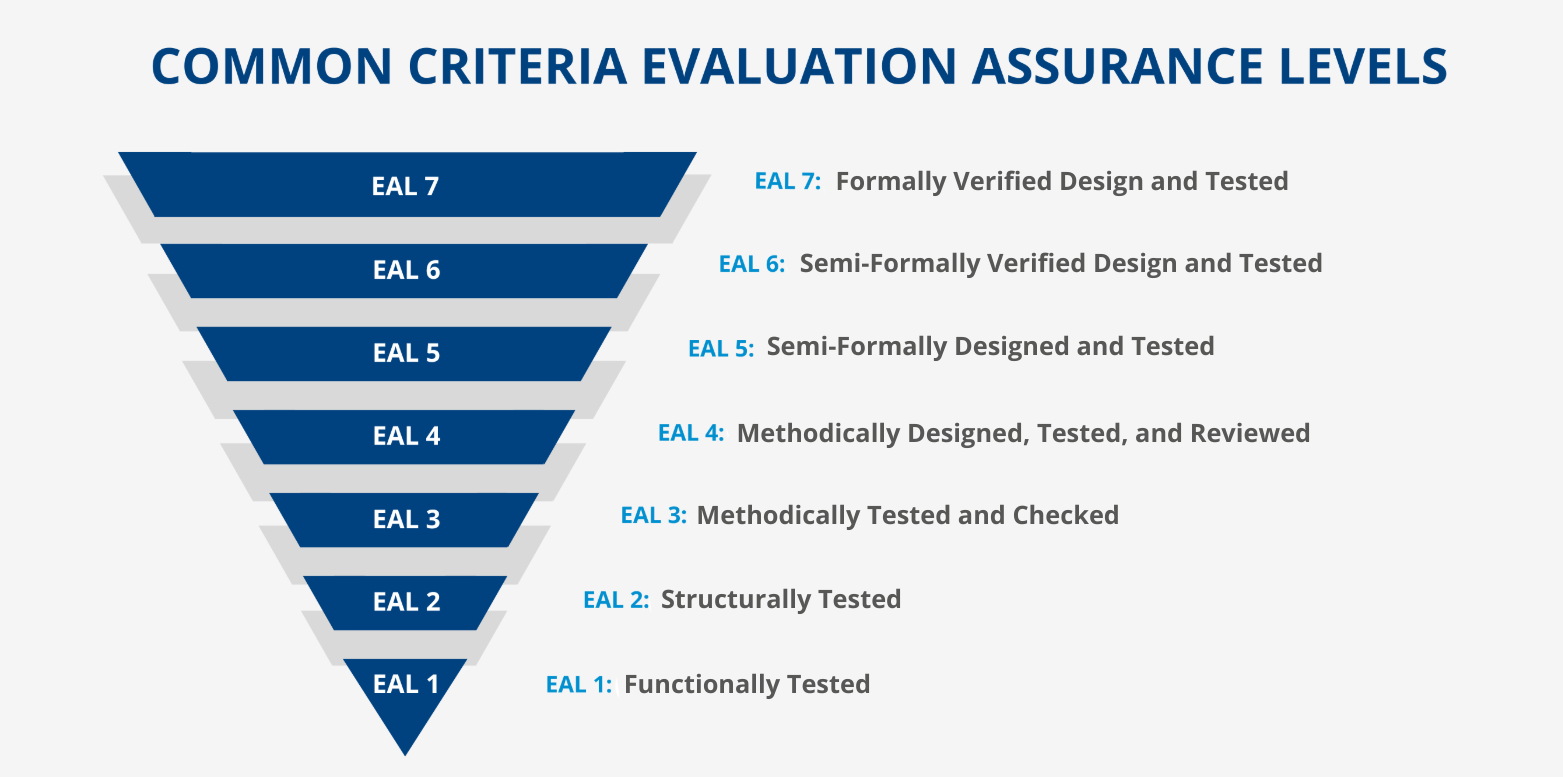
Understanding Evaluation Assurance Level Requirements
The evaluation assurance level framework provides structured approaches to security evaluation. EAL compliance for legacy infrastructure requires careful consideration of system capabilities and security requirements. Organizations must select appropriate EAL levels based on their risk profiles and operational needs.
EAL levels range from basic functionality testing to formal verification methods. Higher levels require more extensive documentation, testing, and analysis. Legacy systems may face challenges meeting higher EAL requirements due to architectural limitations.
For a detailed explanation of the individual Evaluation Assurance Levels, including their structure, objectives, and evaluation depth, explore our earlier article: Common Criteria Assurance Levels: An Overview of the Evaluation Criteria and Methodology.
Organizations should align EAL selection with business requirements and risk tolerance. The chosen level impacts certification timeline, cost, and ongoing compliance obligations. Proper EAL selection balances security assurance with practical implementation considerations.
Practical Recommendations for Certification Success
Immediate Action Steps
Organizations must conduct system inventories immediately. Document all legacy components, dependencies, and security controls. This inventory provides the foundation for certification planning and identifies critical areas requiring attention.
Implement basic security controls where possible. Network segmentation, access controls, and monitoring capabilities provide immediate security improvements. These controls demonstrate security commitment and may satisfy some certification requirements.
Establish monitoring protocols for legacy systems. Enhanced logging, security event correlation, and incident response procedures improve security posture. These capabilities support ongoing compliance and provide evidence for certification evaluators.
Long-Term Strategic Planning
Develop modernization roadmaps that align with certification timelines. Plan phased implementations that minimize operational disruption while achieving security objectives. Consider how to achieve Common Criteria certification for legacy systems through systematic approaches.
Maintain compliance documentation throughout the process. Regular updates ensure accuracy and completeness when evaluation begins. Proper documentation management reduces certification timeline and demonstrates organizational commitment to security.
Engage with accredited laboratories early in the process. Expert consultation identifies potential issues before they become obstacles. Professional guidance accelerates certification and reduces overall project risk.

Accelerating Your Certification Journey
The path to Common Criteria certification for legacy systems demands immediate action and strategic planning. Organizations cannot afford to delay preparation as regulatory requirements continue evolving and compliance deadlines approach.
CCLab’s expertise as an independent, accredited CC laboratory provides the guidance organizations need to navigate certification challenges successfully. During our consulting services the experts will guide you through the Common Criteria requirements, so you can:
- Accelerate preparation
- Save cost and effort
- Avoid mistakes
- Create high quality developer documents
- Prepare your product for a successful certification project
- Maximize efficiency of evaluation
- Spare your organization from unnecessary iterations
Legacy system certification is achievable with proper preparation and expert support. The combination of strategic planning, technical implementation, and professional guidance creates a pathway to certification success. Organizations that act decisively position themselves for compliance success while maintaining operational excellence.
If you’re looking for expert guidance to navigate your legacy system certification, you’ve come to the right place. Contact CCLab today, our team will help you prepare and easily overcome the challenges of the certification process.
Time is critical, start your preparation now to meet upcoming compliance deadlines and secure your organization’s future.
Related downloadables
Related downloadables


Common Criteria Evaluation Process infographics
Common Criteria Evaluation Process infographics
This downloadable infographics introduces the Common Criteria Evaluation process to you. Explore now for free.


EUCC Study - The New European Union Cybersecurity Certification Scheme
EUCC Study - The New European Union Cybersecurity Certification Scheme
Download EUCC Study 2026 for the most important and up-to-date information about the new European Union Cybersecurity Certification Scheme


Guide and Checklist for Common Criteria Evaluations - updated with EUCC Scheme
Guide and Checklist for Common Criteria Evaluations - updated with EUCC Scheme
Learn everything you need to know for a successful Common Criteria certification project. Save costs and effort with your checklist.
Related news

How to Meet IoT Cybersecurity Standards Using the ETSI EN 303 645 Guide
This article provides a comprehensive guide to meeting consumer IoT security standards using the ETSI EN 303 645 framework. It explains why this standard has become the global baseline for compliance, serving as a critical foundation for regulations like the UK PSTI Act and the upcoming EU Cyber Resilience Act (CRA). The post breaks down the 13 essential security provisions, such as banning default passwords and securing software updates, and outlines a structured assessment path from scope definition to accredited testing. Learn how to treat security as a design constraint to avoid market delays, leverage gap analysis for early detection of vulnerabilities, and turn technical compliance into a trusted competitive edge for your smart devices.
5
min reading time

Understanding EUCC Assurance Levels: What “Substantial” and “High” Really Mean for ICT Security
This article provides a strategic guide to the new EUCC assurance levels, explaining what "Substantial" and "High" certifications actually mean for your market access. It demystifies the critical shift from simple EAL numbers to risk-based vulnerability analysis (AVA_VAN), detailing exactly which products require advanced penetration testing versus basic surveys. You will learn how to map your device to the correct assurance category, navigate the new mandatory lifecycle and patching requirements, and avoid the costly trap of over-engineering your compliance strategy.
5
min reading time

Implementing EUCC: What High-Assurance Certification Requires Beyond Traditional Common Criteria Approaches
This is a comprehensive overview of the transition to EUCC (European Common Criteria-based cybersecurity certification scheme). It effectively highlights the shift from the old, fragmented SOG-IS approach to a unified, risk-based framework under the Cybersecurity Act.
8
min reading time
