
Implementing EUCC: What High-Assurance Certification Requires Beyond Traditional Common Criteria Approaches
8
min reading time
Understanding the Shift: From Traditional CC to EUCC
High-assurance certification for cybersecurity products in Europe has entered a new era with the adoption of the European Common Criteria-based cybersecurity certification scheme (EUCC). Formally adopted by the European Union Agency for Cybersecurity (ENISA) in early 2024, the EUCC builds upon the time-proven SOG-IS Common Criteria evaluation framework already utilized across 17 EU Member States. The scheme represents a significant evolution in the EU's approach to cybersecurity compliance, forming part of a broader legislative effort that aligns with the NIS2 Directive and the Cyber Resilience Act. Importantly, the EUCC introduces two distinct levels of assurance based on the level of risk associated with the intended use of products, services, or processes. As highlighted in our previous overview of Common Criteria assurance levels and methodology, understanding these tiers is fundamental to navigating the evaluation process. Furthermore, certifications under this new framework are valid for up to five years, though updates are required when changes occur in the certified product. The European Cybersecurity Certification Group will play an essential role in maintaining this scheme, ensuring its continued relevance and effectiveness. Additionally, as organizations prepare to navigate these new requirements, understanding how the EUCC differs from traditional Common Criteria approaches becomes crucial for achieving compliance and enhancing security posture.

The European cybersecurity landscape has historically been characterized by fragmentation, with different countries operating their own certification schemes and standards. This patchwork approach created significant challenges for manufacturers and consumers alike, necessitating a more unified framework.
Why EUCC was introduced
The European Union Cybersecurity Certification (EUCC) emerged primarily in response to escalating cybersecurity threats and the inadequacies of a fragmented certification landscape within the EU. Before the EUCC, various European countries operated with their own Common Criteria evaluation certification schemes under SOG-IS, creating barriers for businesses operating in multiple countries. The scheme was conceived under the Cybersecurity Act of 2019 to establish a comprehensive and unified framework that enhances cybersecurity standards, creates a safer digital environment, and facilitates smoother trade across the European Union.
Limitations of traditional Common Criteria
Historically, Common Criteria (CC) was designed for a "shrink-wrapped" world where security was evaluated against a static version of a physical or digital product. As technology shifted toward the cloud, several structural "gaps" in the traditional CC framework became apparent. Here is why those limitations existed and how the industry is currently trying to fix them:
The "Point-in-Time" vs. Continuous Delivery Gap:
- Traditional CC: Evaluations are static. Once a product is certified (e.g., EAL4), that specific version is secure. If a vendor changes the code, they often have to undergo a costly "Assurance Continuity" process.
- SaaS Reality: Cloud services and SaaS products use CI/CD (Continuous Integration/Continuous Deployment) pipelines, updating code weekly or even daily. Traditional CC cannot keep pace with this speed without the certificate becoming obsolete immediately.
Systemic and Market Challenges
Beyond the technical mismatch with the cloud, the traditional framework faced several other critical limitations:
- Inconsistent Standards: It created inconsistent security standards across member states despite using similar methodologies.
- Missing Modern Provisions: The framework lacked provisions for emerging challenges like patch management and vulnerability disclosure, which are essential for maintaining security in real-time.
- Market Fragmentation: It required manufacturers to navigate multiple certification processes for different EU markets, increasing administrative burdens and costs.
- Moreover, with the rapid growth of cloud computing and increasing reliance on these services in critical infrastructure, the traditional framework became increasingly outdated.
How EUCC aligns with the Cybersecurity Act
The EUCC represents the first certification scheme developed under the Cybersecurity Act certification framework. It harmonizes certification across Europe, ensuring that all ICT products and services meet a unified security benchmark. Essentially, the scheme serves as the vehicle to convey requirements from EU policy level to industrial service provision and further to users and conformity assessment bodies.
The scheme introduces two levels of assurance based on the level of risk associated with the intended use: "substantial" (covering EAL1 to EAL3) and "high" (covering EAL4 to EAL7). This risk-based approach aligns perfectly with the Cybersecurity Act's goal of establishing appropriate levels of assurance for different scenarios.
By implementing this harmonized approach, the EUCC eliminates previous inconsistencies, simplifies the regulatory environment for manufacturers, and enhances consumer trust in the security of ICT products.
Breaking Down the Assurance Levels
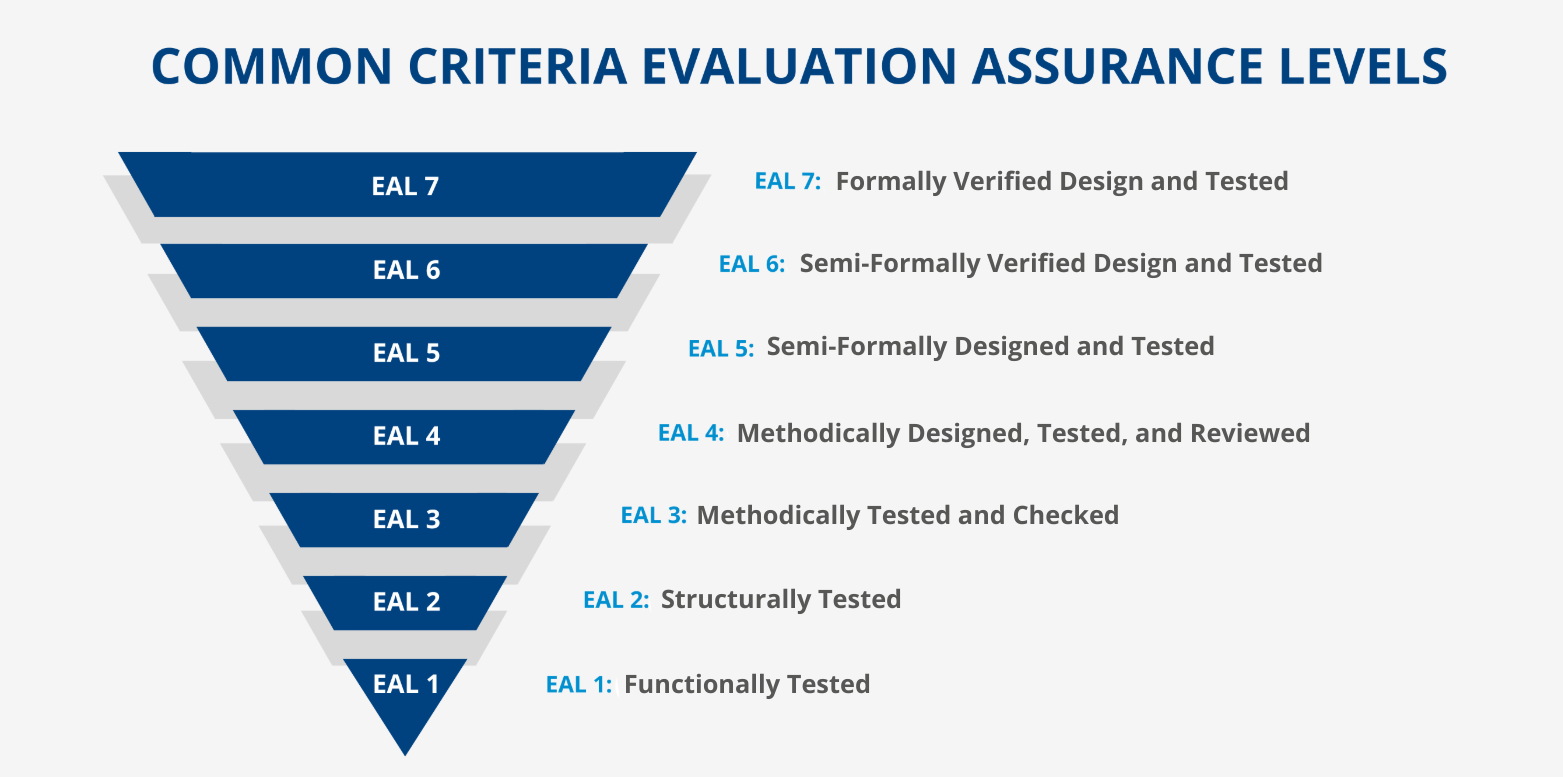
The EUCC framework establishes a clear two-tier structure for assurance certification that directly maps to existing Common Criteria evaluation methodologies while introducing important distinctions in approach. This mapping creates a straightforward pathway for manufacturers already familiar with traditional CC processes.
Substantial assurance: EAL1 to EAL3
The substantial assurance level corresponds to the lower Evaluation Assurance Levels (EAL1 through EAL3) and specifically encompasses vulnerability assessment components AVA_VAN.1 and AVA_VAN.2. At this level, evaluations focus on basic security vulnerability identification through straightforward examination and testing. Specifically, the assessment aims to confirm "the absence of publicly known vulnerabilities" and verify that security functionalities are correctly implemented. This level is intended to minimize “known cybersecurity risks, and the risk of incidents and cyberattacks carried out by actors with limited skills and resources".
High assurance: EAL4 to EAL7
Conversely, the high assurance level corresponds to EAL4 through EAL7, requiring more rigorous vulnerability assessments classified as AVA_VAN.3, AVA_VAN.4, or AVA_VAN.5. This level mandates comprehensive testing methodologies to identify potential vulnerabilities and verify the product's security robustness against state-of-the-art cyberattacks carried out by actors with significant skills and resources. Notably, certification at AVA_VAN.4 and AVA_VAN.5 is reserved for scenarios requiring the highest assurance due to the critical nature of the ICT products. The evaluation activities include reviewing for absence of known vulnerabilities, testing security functionalities, and assessing resistance to skilled attackers through penetration testing.
Dynamic risk-based evaluation under EUCC
Unlike the more static approach of traditional Common Criteria, a shift we recently explored in our guide on what you need to know about security certification in 2025, the EUCC emphasizes current risk contexts, lifecycle support (including patch management), and maintainability. This represents a more modern, flexible certification mindset. The framework allows manufacturers to select appropriate evaluation levels based on the specific risks associated with their products' intended use. This approach aligns with the Cybersecurity Act's goal of establishing appropriate levels of assurance for different scenarios. Additionally, products certified under the EUCC at the "substantial" level or higher qualify for presumption of conformity with the Cyber Resilience Act (CRA).
What High-Assurance Certification Really Requires
While EUCC represents a major step toward harmonized cybersecurity certification in Europe, it does not automatically address every security or assurance gap in all use cases.
Organizations targeting high-risk or highly regulated environments may therefore need to
evaluate whether EUCC alone provides sufficient coverage. A more detailed analysis of
these gaps and limitations is available here: Is EUCC Enough? Addressing Gaps in European Cybersecurity Certification.
Achieving high-assurance certification under EUCC demands significantly more rigor than traditional Common Criteria approaches. Organizations must prepare for an intensive process that extends beyond conventional security testing.
Advanced vulnerability analysis (AVA_VAN.3 to AVA_VAN.5)
The foundation of high-assurance certification lies in comprehensive vulnerability assessment. AVA_VAN.3 introduces thorough analysis to identify vulnerabilities exploitable by attackers with Moderate attack potential (significant skills and resources). This level corresponds to EAL4, which represents a substantial increase in evaluation depth compared to basic assurance levels. At EAL4, the focus is on "Methodical Design" ensuring the product is built following high-quality commercial standards.
For AVA_VAN.4 and AVA_VAN.5 (corresponding to EAL5–EAL7), the scoring methodology becomes increasingly rigorous, shifting the target to resist "High" attack potential. This assumes an adversary with expert-level knowledge and nearly unlimited resources. The analysis evaluates factors such as:
- Elapsed time needed to identify and exploit vulnerabilities
- Specialist expertise required for exploitation
- Knowledge of the Target of Evaluation (TOE)
- Window of opportunity for vulnerability exploitation
- Complexity of required equipment
Key Additions for EAL5:
- Semi-formal Design Modeling: Unlike EAL4’s descriptive approach, EAL5 requires semi-formal notation (such as state machines or specialized diagrams). This eliminates ambiguity, allowing evaluators to mathematically trace security functions directly to the implementation.
- Modular Architecture: EAL5 mandates a modular TSF (TOE Security Functionality). This ensures that security components are isolated, preventing a flaw in one minor feature from compromising the entire secure core.
- Full Source Code Access: While EAL4 often focuses on specific security modules, EAL5 typically requires a more exhaustive review of the source code and hardware logic to ensure no "side doors" exist in the supporting infrastructure.
Formal verification and design rigor
At EAL6, products must demonstrate high-level security engineering with formal verification methods. Semi-formal and formal design specifications must thoroughly describe security functions and their interactions. For EAL7, mathematical verification of design and implementation is mandatory, ensuring security functions are correctly specified and implemented.
The security architecture documentation (ARC) must explain domain separation, initialization processes, and protection against tampering. Particularly for highest assurance levels, formal security models are required to mathematically verify security properties.
Lifecycle security and patch management
The EUCC distinguishes between standard vulnerability management and cases of active exploitation, defined as reliable evidence of unauthorized malicious code execution. In such instances, manufacturers are obligated to inform the Certification Body (CB) without undue delay and prioritize risk mitigation over recertification. The framework emphasizes that patching and correcting the vulnerability must take precedence, utilizing the patch management approaches defined in EUCC Annex IV.
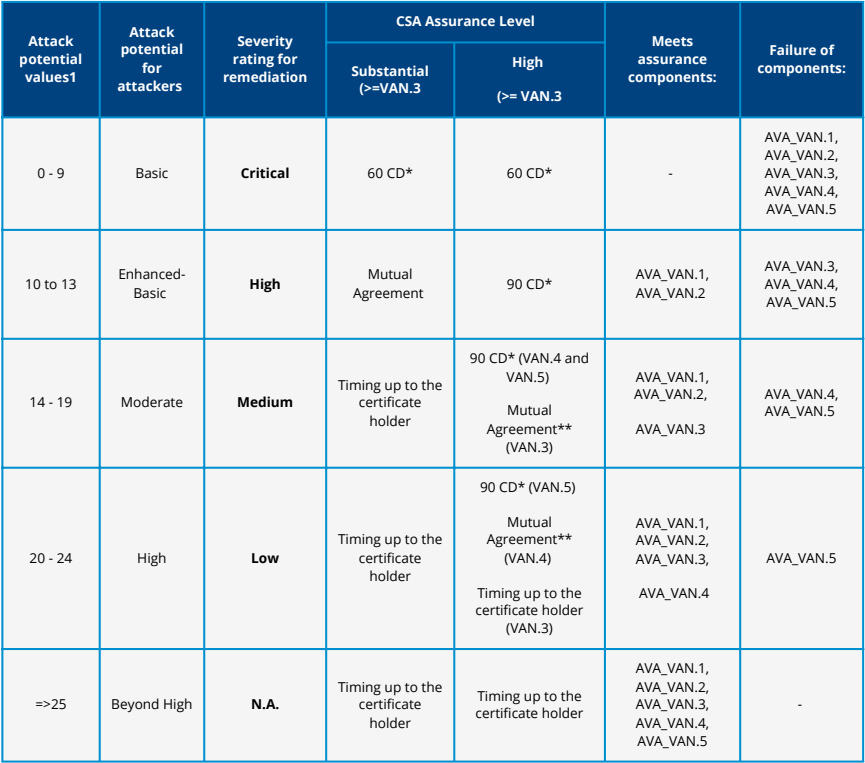
The following table outlines the mandatory maximum timeframes for conducting a vulnerability impact analysis, based on attack potential and severity:
Understanding the Timelines and Extensions
The deadlines indicated in the table serve as recommended maximum limits to ensure timely responses to security threats:
- Critical and High Severity: Reports should be shared as soon as they are available, even before the 60 or 90-day limit.
- Extensions: Timeframes marked with an asterisk may be extended with NCCA approval. A request must be submitted 30 days before the deadline; if the NCCA does not respond within 30 days, the extension is considered accepted.
- Mutual Agreement: This refers to a timeline agreed upon between the CB and the certificate holder, typically when attack potential calculations are borderline. The recommended maximum for such agreements is 180 days.
- Attack Potential Outcomes: If an analysis shows a vulnerability is within the boundaries of the certified AVA_VAN level, further exploit testing is required. If it is beyond those boundaries, the analysis must still be recorded and retained for a minimum of five years.
By adhering to these structured timelines and rigorous impact assessments, including ISO/IEC 18045:2022 attack potential calculations, organizations ensure that high-assurance products remain resilient throughout their entire operational lifespan.
Preparing for EUCC: Practical Steps for Manufacturers
EUCC certification is a structured, multi-phase process designed to deliver high assurance for ICT products operating in risk-sensitive environments. From an executive perspective, predictable outcomes depend on early scoping, realistic planning, and alignment with accredited evaluation and certification bodies.
- Strategic Entry Point:
The process begins with an application to an EUCC-accredited Certification Body. At this stage, organizations define the certification scope, target assurance level, and evaluation boundaries. Early alignment at this point reduces uncertainty later in the process.
- Documentation Readiness: EUCC certification is fundamentally documentation-driven. Technical, architectural, security, and lifecycle documentation must clearly and consistently demonstrate how security objectives are implemented and maintained. Documentation maturity is the primary factor influencing evaluation predictability and effort. A consultant partner can be a good choice to bridge the gap between engineering reality and regulatory expectations, ensuring that internal technical specifications are translated into the precise, audit-ready evidence required to minimize evaluation risks and delays.
- Evaluation Partner Alignment: An EUCC-accredited testing laboratory (ITSEF) is required to conduct the evaluation in accordance with the CC2022 methodology. Many organizations also rely on external expertise to support preparation activities and ensure correct interpretation of EUCC and Common Criteria requirements.
- Evaluation Phase: The evaluation phase consists of structured documentation review, functional testing, and penetration testing, proportional to the selected assurance level. Higher assurance levels require deeper vulnerability analysis and may include site visits to verify lifecycle and operational controls.
- Certification Decision: Upon completion of the evaluation, the Certification Body reviews the Evaluation Technical Report and issues the final certification decision. A successful outcome results in the issuance of an EUCC certificate, confirming compliance with Common Criteria requirements under a harmonized European framework.
- Expected Timeline: While evaluation activities typically take 6–8 months, organizations should plan for approximately 12 months end-to-end, depending on product complexity, assurance level, and preparation maturity.
For a detailed operational overview of EUCC preparation and application steps, see: How to Prepare and Apply for EUCC Certification for Your Product

How CCLab Can Support You
As European cybersecurity certification becomes an increasingly strategic concern, organizations need experienced partners to guide them through the complexity of compliance. As an accredited Common Criteria evaluation lab, CCLab plays a pivotal role in helping companies prepare for and achieve EUCC certification.
CCLab supports clients at every stage of the process from initial feasibility assessments and scope definition to Security Target development, testing coordination, and submission to national cybersecurity authorities. Whether the product is a secure operating system, a cryptographic module, or a trusted cloud component, CCLab ensures that it is evaluated with full adherence to EUCC’s technical and procedural requirements.
Conclusion
The transition from traditional Common Criteria to the European Union Cybersecurity Certification scheme marks a watershed moment for cybersecurity compliance across Europe. Previously fragmented certification landscapes now converge into a unified framework that addresses contemporary security challenges while eliminating cross-border inconsistencies.
Organizations seeking certification must recognize that EUCC demands significantly more than checkbox compliance. High-assurance certification especially requires comprehensive vulnerability analysis, formal verification methods, and robust lifecycle management processes. Companies must therefore assess their product risk profiles carefully before determining whether substantial or high assurance certification aligns with their security objectives and market requirements.
Undoubtedly, manufacturers face a more rigorous path to compliance under this new framework. The scheme's emphasis on continuous monitoring and rapid vulnerability remediation reflects a fundamental shift toward security as an ongoing process rather than a static achievement. This approach acknowledges the reality that security threats evolve constantly, thus requiring corresponding evolution in defensive capabilities.
Preparation stands as the critical success factor for EUCC certification. Thorough documentation, close collaboration with accredited evaluation facilities, and established vulnerability management procedures will determine an organization's certification journey. Additionally, manufacturers must integrate security considerations throughout the development lifecycle, particularly for products targeting EAL4 and above.
Though challenging, EUCC compliance delivers substantial benefits. Products certified under this framework enjoy presumed conformity with the Cyber Resilience Act, streamlining regulatory burdens. Equally important, this harmonized approach builds consumer trust while opening access to markets across the European Union. Ultimately, EUCC certification represents not just a regulatory hurdle but a strategic investment in product security and market positioning as Europe strengthens its cybersecurity posture for the digital age.
Related downloadables
Related downloadables


EUCC Study - The New European Union Cybersecurity Certification Scheme
EUCC Study - The New European Union Cybersecurity Certification Scheme
Download EUCC Study 2024 for the most important and up-to-date information about the new European Union Cybersecurity Certification Scheme
.png)
.png)
Discover the power of CCGuide training course - FREE flyer
Discover the power of CCGuide training course - FREE flyer
This CCGuide flyer will quickly introduce you to the benefits of CCGuide training course subscription for your team. You can be sure that you will be able to use the knowledge you have acquired here and easily pass the CC requirements.
Related news

How to Meet IoT Cybersecurity Standards Using the ETSI EN 303 645 Guide
This article provides a comprehensive guide to meeting consumer IoT security standards using the ETSI EN 303 645 framework. It explains why this standard has become the global baseline for compliance, serving as a critical foundation for regulations like the UK PSTI Act and the upcoming EU Cyber Resilience Act (CRA). The post breaks down the 13 essential security provisions, such as banning default passwords and securing software updates, and outlines a structured assessment path from scope definition to accredited testing. Learn how to treat security as a design constraint to avoid market delays, leverage gap analysis for early detection of vulnerabilities, and turn technical compliance into a trusted competitive edge for your smart devices.
5
min reading time

Understanding EUCC Assurance Levels: What “Substantial” and “High” Really Mean for ICT Security
This article provides a strategic guide to the new EUCC assurance levels, explaining what "Substantial" and "High" certifications actually mean for your market access. It demystifies the critical shift from simple EAL numbers to risk-based vulnerability analysis (AVA_VAN), detailing exactly which products require advanced penetration testing versus basic surveys. You will learn how to map your device to the correct assurance category, navigate the new mandatory lifecycle and patching requirements, and avoid the costly trap of over-engineering your compliance strategy.
5
min reading time

Implementing EUCC: What High-Assurance Certification Requires Beyond Traditional Common Criteria Approaches
This is a comprehensive overview of the transition to EUCC (European Common Criteria-based cybersecurity certification scheme). It effectively highlights the shift from the old, fragmented SOG-IS approach to a unified, risk-based framework under the Cybersecurity Act.
8
min reading time
