
EUCC Behind eIDAS 2.0: The New Pillar of Security in Europe’s Digital Identity Framework
9
min reading time
EUCC Behind eIDAS 2.0: The New Pillar of Security in Europe’s Digital Identity Framework
The European Union has launched an ambitious digital transformation initiative centered on digital identity and trust services. Building upon the foundation of the original eIDAS Regulation (Regulation (EU) No. 910/2014), the updated eIDAS 2.0 framework (Regulation (EU) 2024/1183) establishes a European Digital Identity (EUDI) Framework that requires all Member States to make interoperable EU Digital Identity Wallets available to citizens and businesses by 2026. This effort aims to create consistency in legal certainty, interoperability, and data protection across borders, strengthening trust in Europe’s digital landscape.
Behind this transformative initiative stands the EUCC (European Cybersecurity Certification Scheme) , the emerging security foundation that strengthens technological trust within Europe’s digital identity ecosystem. As one of the first EU-level certification schemes developed by ENISA under the Cybersecurity Act, EUCC aims to establish harmonized and mutually recognized cybersecurity assurance standards across all Member States. Building upon the legacy of the Common Criteria (EAL1–EAL7) framework, EUCC introduces a consistent and transparent evaluation methodology that enables ICT products, including those supporting eIDAS 2.0, to meet stringent protection and assurance requirements.
The central objective of these combined regulations is to enable individuals and organizations to authenticate themselves, exchange trusted attributes, and sign legally binding documents across Member States without friction. Furthermore, eIDAS 2.0 aims to put personal data sovereignty back in the hands of citizens while ensuring a level playing field in the use of trust services throughout the EU in line with GDPR Article 24. This article explores how EUCC strengthens eIDAS 2.0, what this means for manufacturers and end users, and why this certification system represents a critical evolution in Europe's digital identity landscape.
Understanding eIDAS 2.0
The new Regulation establishing a framework for a European Digital Identity builds on the 2014 Regulation on electronic identification and trust services for electronic transactions in the internal market (eIDAS Regulation).
eIDAS stands for electronic IDentification, Authentication and trust Services that aims to make electronic transactions more secure and trustworthy within the territory of the Union. It offers a standardized approach and a common blueprint for secure electronic interactions, such as payments or administration, between private individuals, businesses and public authorities nationally and internationally alike.
The original eIDAS framework relied on a complex, multilayered infrastructure connecting national systems, which often led to interoperability and reliability issues. As digital interactions expanded beyond public administration to include the private sector, the EU recognized the need for a new, scalable framework capable of supporting both governmental and commercial use cases.
This realization laid the foundation for eIDAS 2.0, a regulation designed to strengthen trust, simplify technical integration, and extend digital identity usability across the entire European market.
A key innovation in eIDAS 2.0 is the introduction of the European Digital Identity Wallet (EUDI Wallet), which will give every EU citizen and business access to a recognized and interoperable digital identity usable across all Member States. This wallet enables users to securely store and share only the necessary personal data, enhancing privacy and control.
In addition, eIDAS 2.0 expands the Trust Services ecosystem by adding new qualified services such as electronic certificates, signatures, seals, credentials, and certified electronic archiving, strengthening the legal validity and security of digital transactions throughout the Single Market.
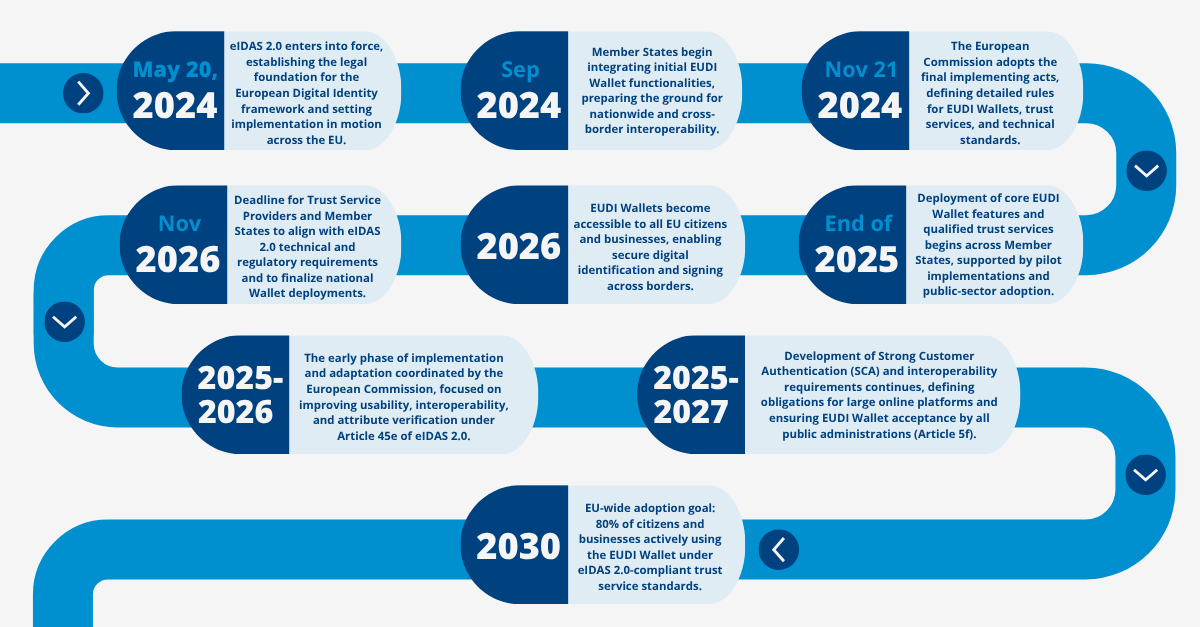
The eIDAS 2.0 regulation officially entered into force on May 20, 2024. Under this framework, every EU Member State must make available at least one European Digital Identity Wallet (EUDI Wallet) to citizens and businesses by 2026.
The initial integration phase began as early as September 2024, with Member States progressively deploying the first wallet functionalities. By the end of 2025, the core trust services, including authentication, verification, and secure attribute exchange, are expected to be fully operational across participating countries.

What is EUCC and Why It Matters
The European Union Cybersecurity Certification, drafted by ENISA (European Union Agency for Cybersecurity), is a monumental leap forward in certifying Information and Communication Technology (ICT) products within the European landscape and at the EU level.
Conceived under the EU Cybersecurity Act, enacted in 2019, this groundbreaking scheme is designed to revolutionize the cybersecurity certification process for a wide spectrum of ICT products, covering hardware, software, and services. The overarching goal is to establish a comprehensive and unified framework that enhances cybersecurity standards, creates a safer digital environment for consumers, and fosters smoother trade across the European Union.
For a more detailed overview of the EUCC framework, refer to our blog post “EUCC: A New Cybersecurity Scheme for Evaluating and Certifying Products in Europe.”
So, the EUCC’s objective is to:
- harmonize cybersecurity certification requirements across the European Union,
- provide a unified and transparent evaluation process for manufacturers and laboratories, and
- strengthen Europe’s digital trust infrastructure, which also serves as a foundation for eIDAS 2.0.

How EUCC Strengthens eIDAS 2.0
At the core of Europe’s digital identity evolution lies a critical connection between the EU Cybersecurity Certification Scheme (EUCC) and the eIDAS 2.0 framework.
While eIDAS 2.0 defines the legal and functional rules for digital identity, EUCC provides the technical assurance layer that reinforces trust across the European Digital Identity ecosystem.
- The link between EUCC and the EUDI Wallet
EUCC supports the security foundation of the European Digital Identity Wallet (EUDI Wallet), the centerpiece of eIDAS 2.0.
This connection is intentional, European policymakers increasingly refer to cybersecurity certification schemes such as EUCC to ensure consistent implementation of new cyber legislation.
As Member States develop their national wallets for rollout by 2026, EUCC offers a structured, harmonized validation framework that fosters cross-border trust and interoperability.
- Ensuring secure digital identity components
The EU Cybersecurity Act establishes a European-wide certification framework for ICT products and services, with the EU Cybersecurity Certification Scheme (EUCC) as one of its cornerstone initiatives.
Building on the well-established Common Criteria (ISO/IEC 15408) methodology, EUCC introduces a harmonized European governance model under ENISA’s supervision, ensuring that ICT products used for trust services and digital identity management meet consistent, high-assurance security standards across all Member States.
One of EUCC’s defining features is its structured, multi-level assurance model, derived from the Common Criteria approach.
These Evaluation Assurance Levels (EAL1–EAL7) represent varying depths and rigor of security assessment, providing a scalable measure of confidence in a product’s resistance to vulnerabilities and cyber threats.
Each level corresponds to an increasing degree of assurance, complexity, and testing intensity.
In the context of eIDAS 2.0, these Common Criteria Assurance Levels ensure that devices used for trust services, such as electronic signatures, electronic seals, and timestamps, are evaluated to meet stringent security standards.
The appropriate level of assurance is selected based on the risk and sensitivity of the service. For instance, a qualified electronic signature creation device, which must provide the highest level of legal certainty, would typically require an evaluation at a higher Assurance Level to ensure it can withstand sophisticated attacks.
- Supporting trust service providers
Within the eIDAS 2.0 ecosystem, trust service providers, offering services such as digital signature services, electronic seals, timestamps, etc., must meet stringent security requirements to ensure the integrity, confidentiality, and availability of their services.
The EUCC scheme supports this by enabling the certification of the ICT products, cryptographic modules, and signature creation devices used by these providers.
For example, a Qualified Signature Creation Device (QSCD) used under eIDAS 2.0 can undergo EUCC certification, ensuring it complies with EU-level cybersecurity assurance and protection standards.
- Technical assurance and legal coherence
EUCC bridges technical assurance and regulatory coherence by introducing uniform security standards across all EU Member States.
This harmonized approach ensures consistent evaluation of digital identity technologies and reduces fragmentation between national regulations.
As a result, eIDAS 2.0 achieves both legal certainty and technical resilience, laying the foundation for a secure, interoperable European digital identity framework.

Compliance Deadlines and Steps for Companies
For European companies, waiting is not an option. Businesses must immediately assess their digital identity processes and act decisively to ensure compliance with eIDAS 2.0.
Delays risk regulatory penalties and missed opportunities to build trust, streamline operations, and compete effectively in the EU digital market. Proactive preparation is essential to secure your future success.
How can CCLab help?
Looking for expert guidance on eIDAS compliance?
Check out our eIDAS service page to see how CCLab can help your organization achieve certification efficiently.
We are experienced in:
- Conformity Assessment and Consultation for qualified trust service providers (QTSP) within the European Union.
- Common Criteria Evaluation for qualified signature and seal creation (QSCD) devices (both client and server side) according to Commission Implementing Decision 2016/650.
- Common Criteria Evaluation of the software environment of remote electronic qualified signature according to eIDAS Article 30. (3) b)
Our team supports developers and manufacturers through every step of EUCC and eIDAS 2.0 compliance.
Schedule your free consultation to discover how we can help your product achieve certification across Europe.
Conclusion
Integrating EUCC with eIDAS marks a significant step toward improving the security, interoperability, and trustworthiness of electronic identification and trust services across the EU. This collaboration not only facilitates cross-border digital transactions but also promotes a cohesive digital single market where services are recognized and trusted throughout member states. As the digital landscape continues to evolve, integrating these two frameworks will play a crucial role in ensuring the safety and efficiency of electronic interactions within the EU.
Related downloadables
Related downloadables


EUCC Study - The New European Union Cybersecurity Certification Scheme
EUCC Study - The New European Union Cybersecurity Certification Scheme
Download EUCC Study 2024 for the most important and up-to-date information about the new European Union Cybersecurity Certification Scheme


Guide and Checklist for Common Criteria Evaluations - updated with EUCC Scheme
Guide and Checklist for Common Criteria Evaluations - updated with EUCC Scheme
Learn everything you need to know for a successful Common Criteria certification project. Save costs and effort with your checklist.


Common Criteria Evaluation Process infographics
Common Criteria Evaluation Process infographics
This downloadable infographics introduces the Common Criteria Evaluation process to you. Explore now for free.
Related news

Cyber Resilience Act & EUCC Explained: Key Differences, Overlaps and Compliance Pathways
As the 11 September 2026 reporting deadline approaches, understanding the Cyber Resilience Act (CRA) is essential for all manufacturers of digital products. This blog post explores the key differences and overlaps between the CRA and the EUCC certification scheme, providing a clear roadmap for compliance, risk categorization, and long-term market access.
9
min reading time

Preparing Legacy Systems for Common Criteria Certification
Legacy systems power critical operations across industries worldwide, yet they present unique challenges when organizations pursue Common Criteria certification. The clock is ticking for manufacturers and enterprises who must navigate complex compliance requirements while maintaining operational continuity. Organizations pursuing Common Criteria certification must address unique challenges when dealing with legacy infrastructure, but with the right approach, success is achievable. The urgency cannot be overstated. Regulatory deadlines approach rapidly, and the cost of non-compliance continues to escalate. Legacy systems that once served as reliable workhorses now require strategic transformation to meet modern security standards. This guide provides actionable strategies to prepare your legacy infrastructure for certification success.
10
min reading time

EUCC Behind eIDAS 2.0: The New Pillar of Security in Europe’s Digital Identity Framework
The European Union has launched an ambitious digital transformation initiative centered on digital identity and trust services. Building upon the foundation of the original eIDAS Regulation (Regulation (EU) No. 910/2014), the updated eIDAS 2.0 framework (Regulation (EU) 2024/1183) establishes a European Digital Identity (EUDI) Framework that requires all Member States to make interoperable EU Digital Identity Wallets available to citizens and businesses by 2026. This effort aims to create consistency in legal certainty, interoperability, and data protection across borders, strengthening trust in Europe’s digital landscape.
9
min reading time
